Lock-free WiFi security features + VPN security issues. Seven tips for safe surfing the Internet to avoid risks.
“Cybersecurity for the people, cybersecurity depends on the people.”
To maintain network security, it is an important part of the majority of netizens to improve their network security awareness and protection skills.
February 1, 2023 marks the first anniversary of the implementation of the Cybersecurity Law.
In the past year, a number of illegal websites and accounts have been shut down, some platforms that have failed to protect network security have been held accountable, a series of cybercrime cases have been detected, and the network environment has become more secure. Lock-free WiFi security features + VPN security issues
Lock-free WiFi security features + VPN security issues
Today, when network security is getting more and more attention, what are the precautions in the sea of networks and how to avoid security risks?
Free WiFi should be careful, privacy should be guarded, network payment should be verified, password modification should be regular, suspicious links should not be clicked, social information should not be leaked, and antivirus software should be updated frequently.
The new media version launched a special plan of “Safe Internet Access: Seven Ways to Help You ‘Demine'” to help netizens improve their awareness of cybersecurity, better use technology and legal weapons, and work together to maintain cybersecurity.
Lock-free WiFi security features
Free WiFi should be used with caution
Netizens said: When waiting for the subway, there is nothing to do on the Internet. I found a free WiFi signal on my phone, entered my phone number, and received a verification code.
Who knew that after half an hour of logging in, the phone would shut down.
At first, I thought that the monthly rent balance was not enough, and I transferred tens of yuan into it and still stopped. Calling to ask customer service, I learned that the mobile phone had been charged ¥500 for Internet access.
VPN WiFi router
Some free, unlocked WiFi security protection found in public places is weak, do not covet the small bargain of sharing WiFi, resulting in the theft of bank card information, application account passwords, etc. on the mobile phone.
Try not to use WiFi hotspots without verification or passwords from unknown sources; If you need to use it, it is recommended to set the WiFi connection to manual and open a secure VPN channel, and remember to log in through a dedicated APP client for online banking, Alipay, etc.; When not using WiFi, it is best to turn off the WiFi auto-connect feature.
Non-public places, including your own router, must also enable wireless network encryption to prevent people from surfing the Internet or monitoring your network without consent.
Carefully select and use smart IoT devices, most of which still rely on mobile apps to obtain network credentials.
Beware of privacy calls
Netizens said that once downloaded a mobile game, and when installing, a pop-up window popped up to remind you to obtain several privacy permissions, including calling call records, accessing address books, etc., although some puzzled but still checked.
VPN tunnel ISP – vpn tunnel explained
But after a while, I received an SMS reminder that the phone was set up for call forwarding, and I realized that my personal information had been stolen by shady software.
Calling some privacy permissions is a necessary step for the operation of mobile apps, but excessive rights may lead to privacy leakage.
When installing mobile phone software, carefully read the privacy policy to clarify what privacy permissions the mobile phone software calls, especially whether it involves sensitive permissions such as accessing SMS records, modifying call records, and turning on microphones or cameras.
In the event of excessive demand, consider abandoning the installation in favor of other software.
On weekdays, you should manage privacy authorization and turn off unnecessary or potentially dangerous authorization options.
In addition, open pages such as “personality test”, “praise lottery”, “help haggle”, etc., you should always be vigilant and do not fill in information such as mobile phone number and ID number at will.
Payment security find regular
Netizens said: The day after online shopping, I received a call from the so-called customer service, saying that the transaction of the purchased goods was unsuccessful.
Log in to your shopping account and find that the purchased goods are indeed missing, so you “register” the bank card number, password and other information at the time of payment according to the other party’s requirements, and truthfully inform the three mobile phone verification codes received. Unexpectedly, I soon found that my bank card deposit was transferred.
When shopping online, be sure to choose reputable merchants and regular apps.
Log in to the shopping website, first verify whether the website domain name is correct, pay attention to the payment website at the beginning of “https://”, and most of them will have anti-counterfeiting security signs such as padlocks, and carefully fill in sensitive information such as names, ID numbers, bank accounts, etc.
Do not click on the URL link in the SMS at will, cautiously click on all kinds of links sent by the merchant from the instant messenger, and beware of phishing websites.
The payment app only binds a small bank card, remember to unbind the bank card before deleting the app. Consider downloading the Mobile Manager and PC Manager software with installation specifications to help identify.
Regular revision should not be simple
Netizens said: When I was on a business trip, I accidentally lost my mobile phone. At first, I didn’t pay attention, but when I finished replacing the mobile phone card, I found that WeChat Pay had been trading for a few days when the mobile phone was lost, and it was swiped nearly ¥20,000.
Later, I learned that although the boot password and payment password were set, the password was too simple, and the other party tried out the password several times after picking up the mobile phone.
When setting a password, avoid using simple and regular numbers or letter combinations, such as “123456” and “abcde”, and try to avoid using name pinyin or abbreviation, birthday, mobile phone number, and part of the certificate number as the basis for setting the password.
In daily use, develop the habit of changing the password regularly, and manage it according to the importance of the account and whether property is involved, etc., to avoid multiple uses of one code.
In addition, when logging in to your personal account on public devices, be careful not to check the options such as “remember password” and “default login”, choose anonymous login as much as possible, and try not to use online banking on public devices or enter passwords such as bank account and Alipay.
Be wary of copycats to verify first
Netizens said: A WeChat friend sent a screenshot of the lottery winning, and I was very moved to see it, so I opened a link to a lottery website in the picture.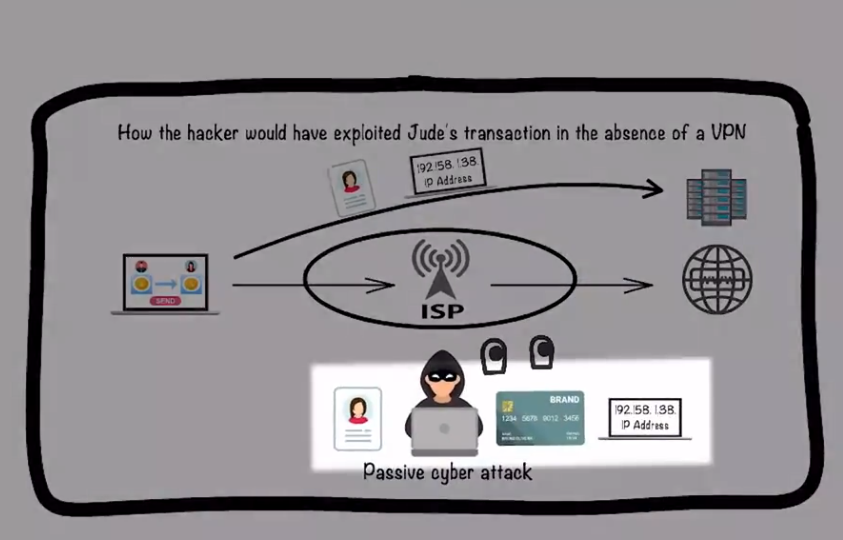
Under the guidance of the website, register an account, recharge to buy lottery tickets, get a small profit and continue to recharge, and lose hundreds of thousands of dollars and get nothing.
Only then did I find out that it was a “Li Ghost” lottery website, and it had long been monitored by the background.
The formal website page is standardized, the information is complete and there is a large amount of original content, and the ICP filing number and ICP certificate number of the website will generally be provided at the bottom of the homepage of the website; Informal websites, on the other hand, generally use templates and modular structures to confuse the public.
Don’t click on download links or QR codes that don’t have a trusted and secure source, look for safe large, third-party app marketplaces or official download links.
Scammers are most likely to play charities and send relevant copycat links; Beware of QR code scams such as “scan code to give gifts” and “scan code to focus on entrepreneurship”, and don’t be greedy for small bargains.
When encountering a fake link scam, you should report to the police in time and keep relevant records to prove it.
Personal information is not indiscriminate – WiFi security features
Netizens said: During the New Year, I received a text message from a stranger saying “Happy New Year, I sent the photos of the last party to the online disk, the link will be sent to you”.
I opened the link in the text message and found that it was a blank page, thinking it was a network problem, however, soon a friend received a text message from my mobile phone number requesting to send money, which reflected that the mobile phone had a virus.
Do not easily open the so-called “important documents”, “award links” and “wonderful pictures” and other information, links or pictures from unfamiliar numbers, and avoid opening emails and attachments from unknown sources.
In the use of computers, mobile phones and other equipment, install necessary anti-virus software and firewalls, regularly check and kill viruses on mobile phones and computers, and clean up Trojan viruses or malicious programs.
Update operating systems, browsers, and third-party applications in a timely manner to prevent hackers from exploiting vulnerabilities to launch malicious attacks.
Habit of regularly backing up important data files to minimize the loss and impact of virus attacks.
Investigate poison and build a safety valve
Netizens said: I received a private message from a “Weibo friend” traveling in a certain country, asking for help to contact the manager of an airline to check whether the booked ticket was successfully reserved, and provided the “manager” mobile phone number.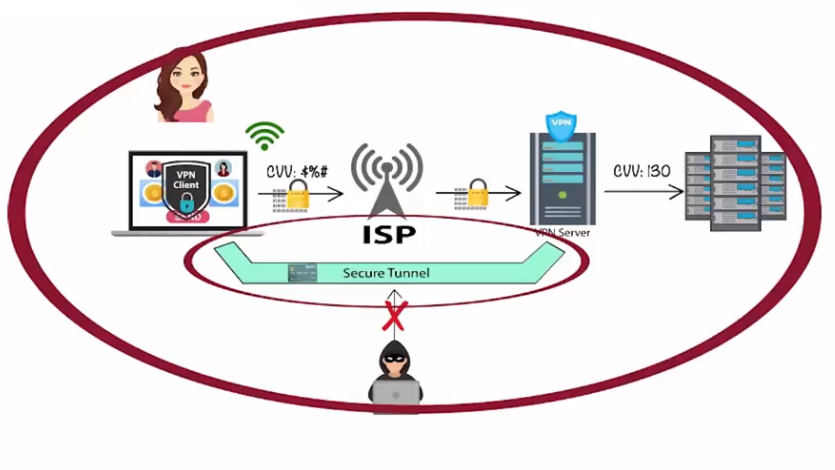
VPN ISP – VPN tunnel definition – Lock-free WiFi security features + VPN security issues
After contact, I was told that the ticket had not been paid, and the “friend” was unable to transfer money for some reason to help pay in advance, and as a result, he was deceived.
In social networks such as Weibo, QQ space, Tieba and forums, avoid revealing or marking real identity information as much as possible; Do not add unknown friends on social platforms such as WeChat, be wary of advertisements, help haggling, help voting and other links sent by “most familiar strangers”, and share personal information at a minimum; Do not post resume, contact address, documents, tickets, location, family and other information on social networks.
Criminals will study the social habits and other information of the target victim to carry out precise fraud, and it is difficult to distinguish high-imitation social accounts.
After encountering fraud, save the chat history and report to the police in time.












